Reset Domain Crossing Tools – Reviews & Metrics
Reset domain crossing (RDC) sign-off tools perform structural and functional analysis to ensure that signals crossing reset domains are received reliably. This article captures reset domain crossing reviews by users for the industry’s most popular RDC products.
What is RDC Sign-Off?
Reset domain crossing sign-off requires analysis, debug, modifications and verification that the data is properly transferred across reset domains, without introducing design problems that could cause design failures.
As part of this, reset domain crossing tools analyze:
- Do asynchronous resets cause metastability when activated or deactivated?
- Are two events that propagate from one reset functionally correlated when software resets assert or de-assert?
- Are asynchronous resets glitch-free, avoiding an intermediate wrong value for a cycle at the destination flop?
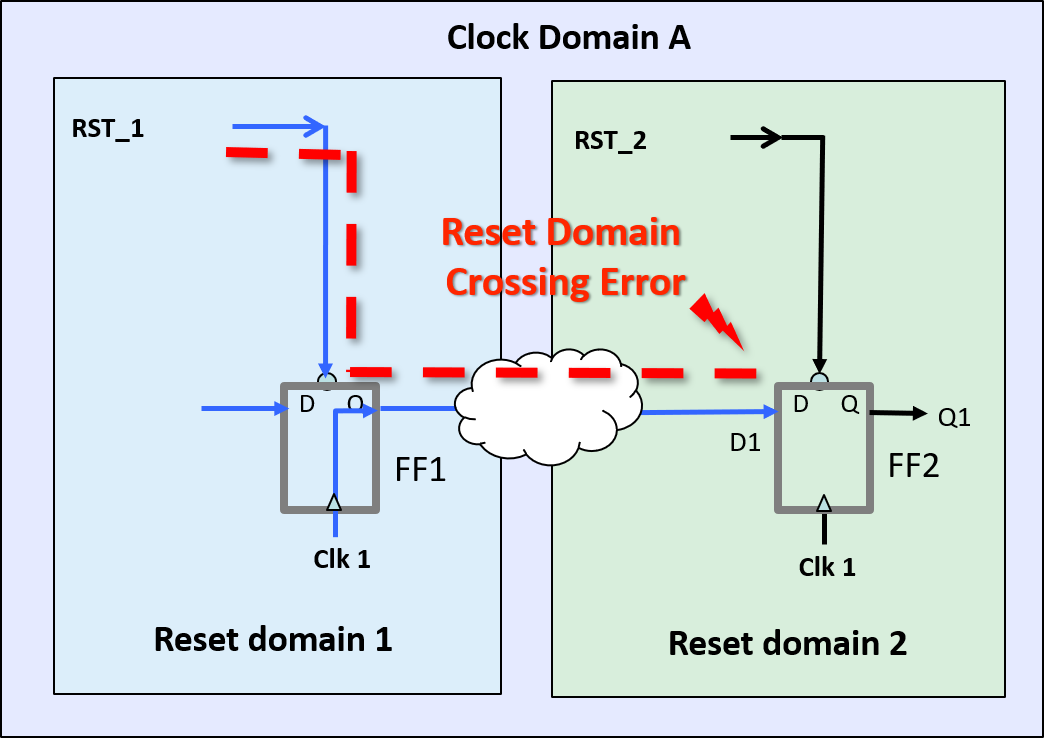
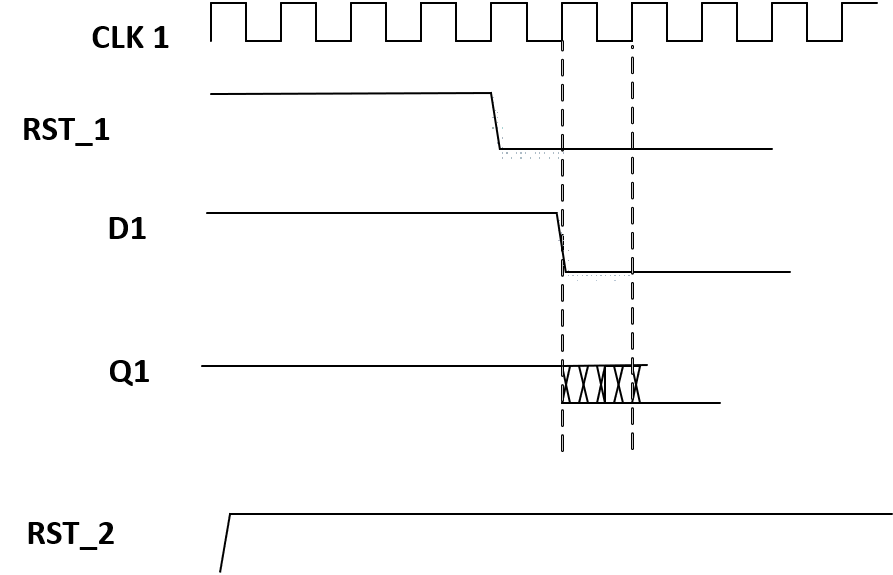
RDC Metastability Example:
Assertion of RST_1 creates untimed path from FF1 to FF2. This causes metastability when RST_1 asserts and RST_2 to FF2 is de-asserted.
Reset Domain Crossing Reviews
There are multiple commercial tools that will address RDC analysis and verification throughout the design process. Below are detailed user reviews on the most commonly used reset domain crossing tools from DeepChip.com’s ongoing user tool discussions and the annual EDA user reports.
The dates are based on the year the reviews were published.
The reset domain crossing reviews include: Real Intent Meridian RDC & Synopsys SpyGlass RDC.
Reset Domain Crossing Tool Metrics
Below are the primary metrics and criteria that the system and semiconductor design & verification engineers referenced when reviewing the products.
RDC Tool Metrics Covered
- Ability to find 100% of targeted failures.
- Noise. The relative ratio of false positives to errors in the violation reports.
- Runtime performance & capacity.
- Debug usability. Schematic views of violation. Violation filtering.
- Constraint verification. Set up checks & SVA assertions.
