Connectivity Sign-Off: 5 Ways to Prevent Costly Errors
I. Overview: Connectivity Static Sign-Off is Part of Design Sign-Off
Connectivity static sign-off is becoming a critical aspect of a design sign-off.
This article covers five connectivity verification and sign-off requirements needed to stop connectivity error escapes while minimizing engineering time – especially as the connectivity requirements can vary between designs.
What is Connectivity Sign-Off?
Connectivity sign-off is an exhaustive verification process which ensures that the paths between specified sources and destinations are properly connected and do not go through disallowed logic or connect unspecified sources or destinations.
II. Connectivity Sign-Off: 5 Ways to Prevent Costly Connectivity Errors
1. Use Comprehensive, Design-Specific Tiered checking
Connectivity sign-off applies connectivity rules during progressive design stages to meet the functional specifications for each design. The connectivity rules could be as simple as a signal driving a set of flops, or more complex checks at the architectural level.
1a. Need user-defined comprehensive ruleset
To achieve sign-off, it’s critical to have a comprehensive set of rules. For example, an industry standard bus with multiple drivers and receivers may need to have different connectivity depending on the design mode. Additional connectivity checks might be that all sources are connected to all destinations, only one source is connected to the specified set of destinations, etc.
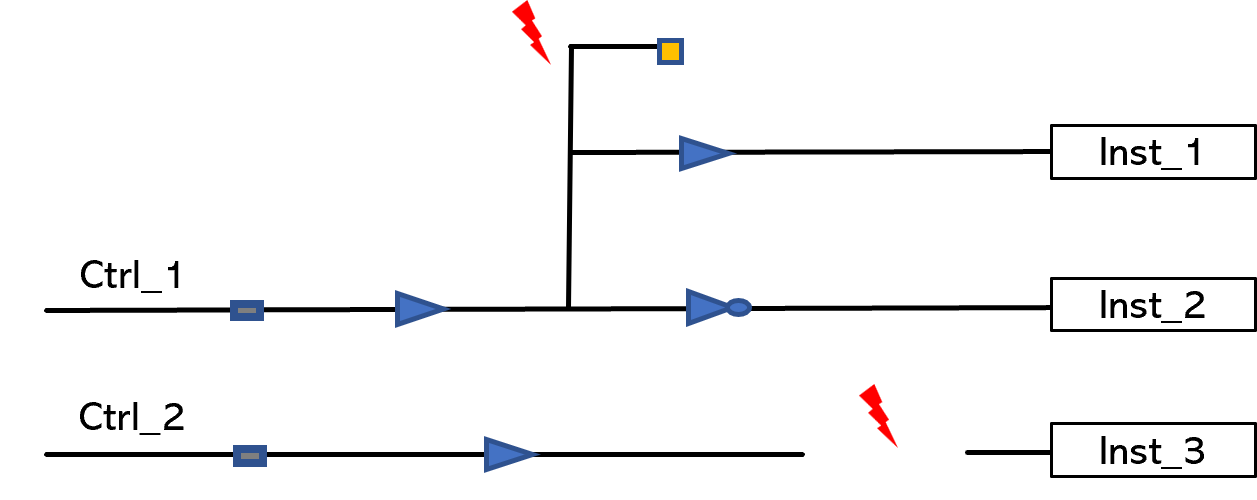
Example 1. Check that the connectivity between two flip-flops exists or does not exist.
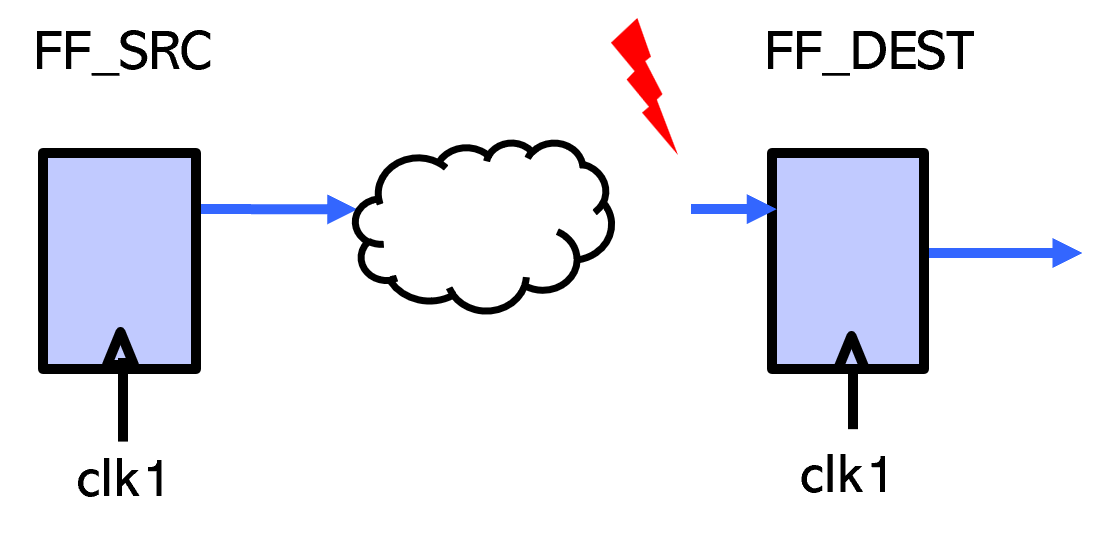
Connectivity should exist between FF_SRC & FF_DEST
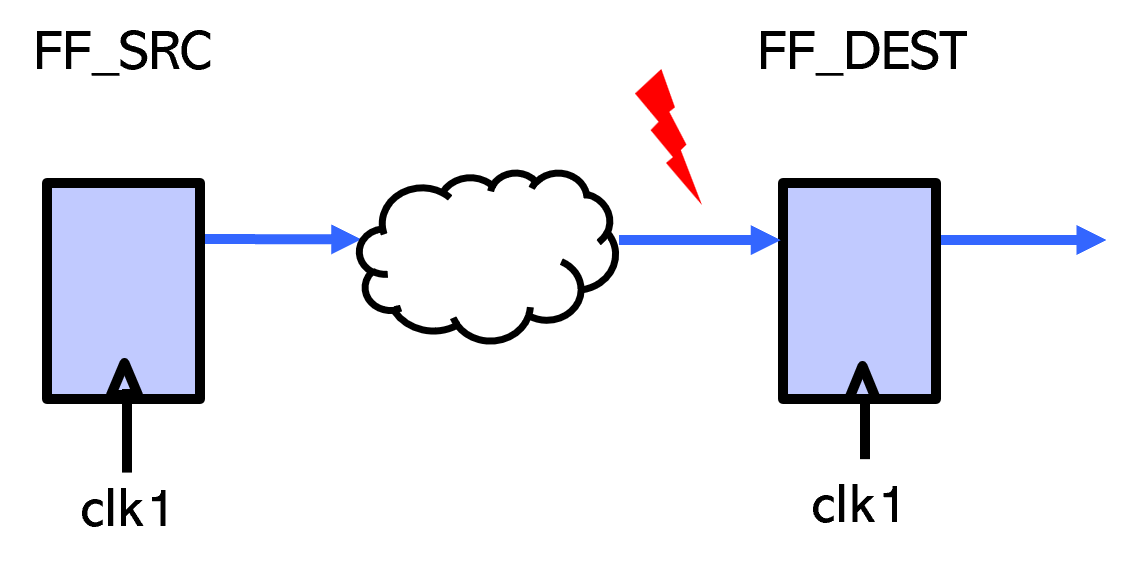
Connectivity should not exist between FF_SRC & FF_DEST
Example 2: Check that source bus [0:3] is connected to destination bus [0:3] without any bit swapping.
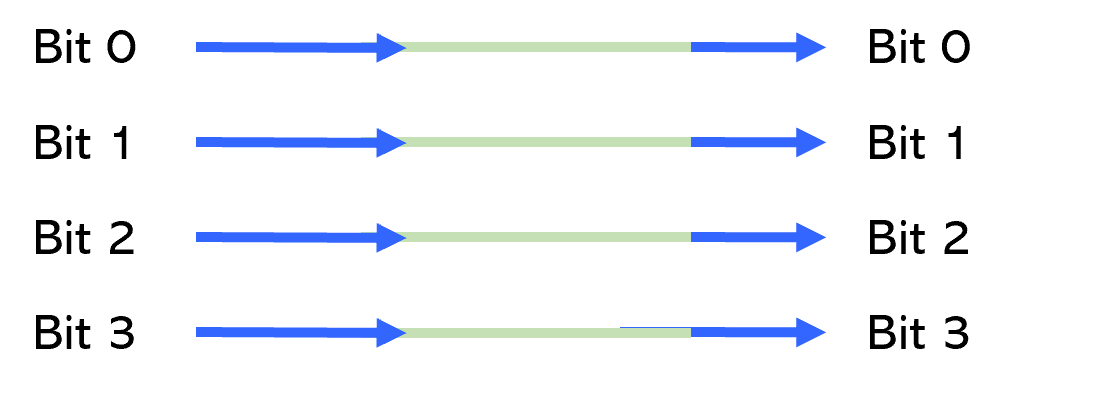
Expected connectivity
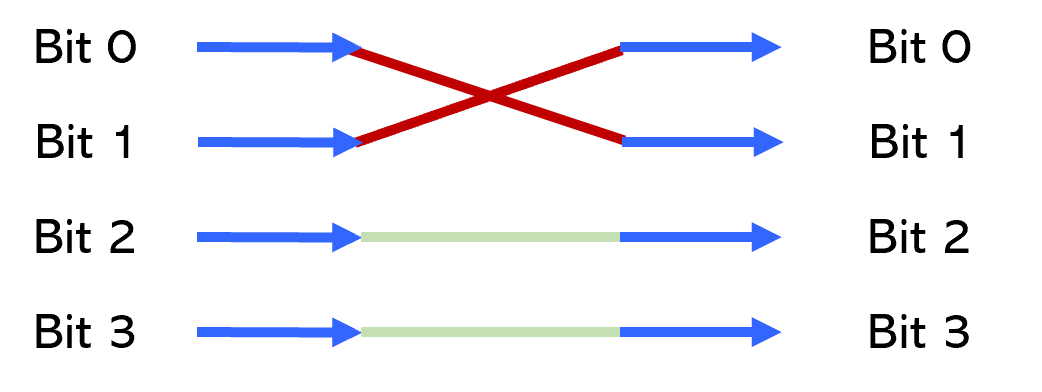
Bit swizzle error
Example 3: Check for mutually exclusive driver/receiver connections
If the design has a connection from A to C, then a connection from B to C is not allowed.
The engineer should check for both the connections – one existing and the other not existing.
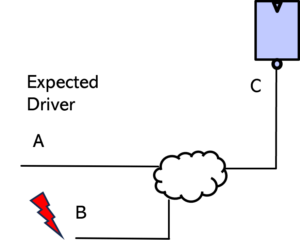
Mutually exclusive driver connection
1b. Create groups, define clear rules & granular sub-checks
The most efficient way to build a connectivity checking ruleset is to first create groups to aggregate objects for checking, based on sources, destinations, and path tracing control.
For example, to ensure UPF power schemes are implemented correctly, group all isolation cells and check the connectivity using that group.
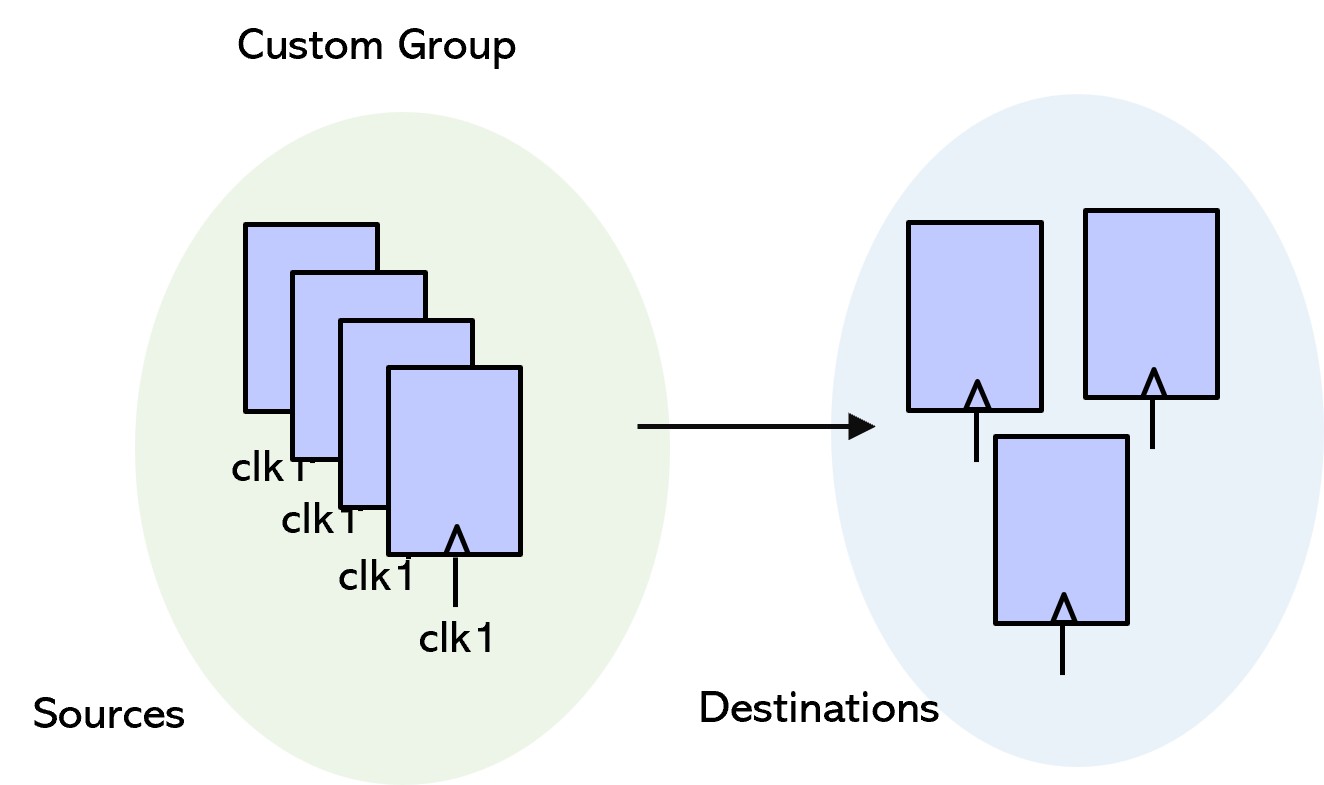
Another way is to use connectivity commands to automatically create custom groups. For this, define and apply clear connectivity rules with granular sub-checks in a tiered manner. Start by creating source (S1) and destination (D1) groups, then apply connectivity checks step-by-step, as shown in this example.
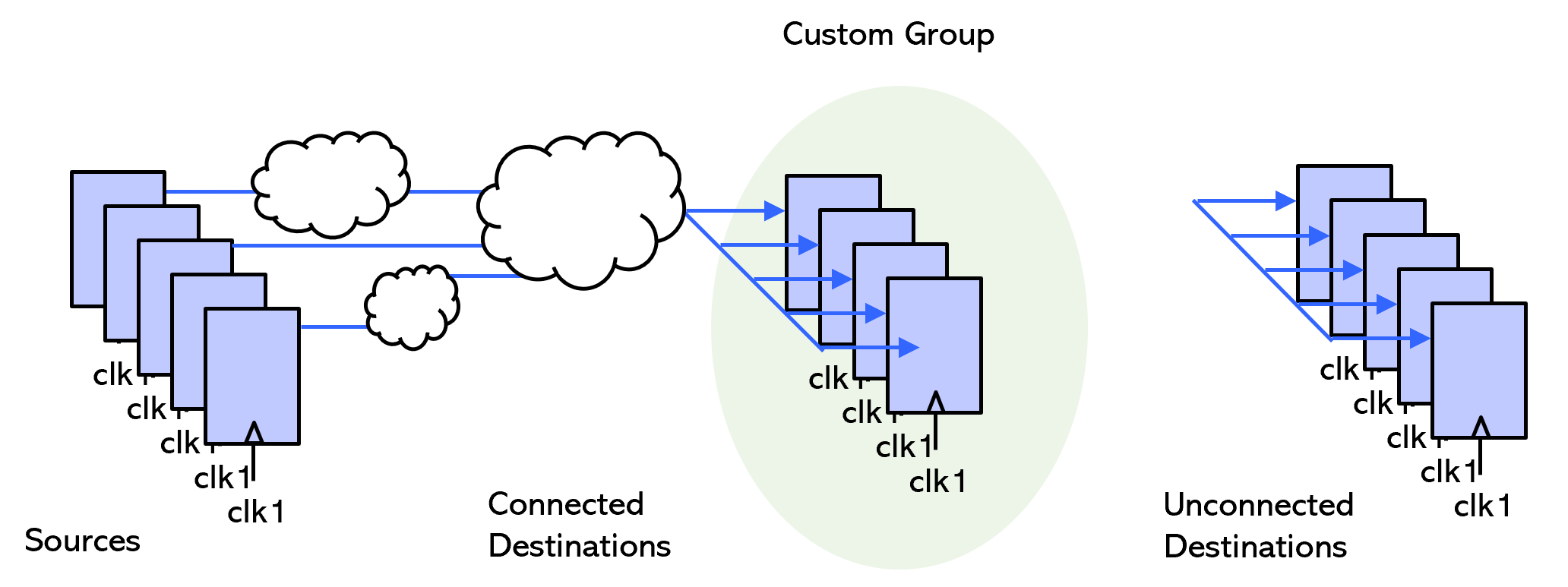
Check connection – Step 1
Check connectivity, e.g., 4 out of 9 instances are connected. Filter the 4 connected signals/instances into a new custom group.
Check connection – Step 2
Run another connectivity check using the custom group; the prior destinations included in that group are now sources for further checks.
1c. Define rules to avoid redundancy
Connectivity rules should be defined such that there is no redundancy in checking the same source and destination for different violation types.
Paths from source to destination can be checked for not having combo logic in one rule and then checked for extra fanouts in another rule. Precisely combining this functionality in one rule avoids redundancy to improve analysis and user review efficiency.
2. Perform early connectivity sign-off to eliminate critical verification holes at later design stages
It’s important to begin connectivity static sign-off early – before simulation or synthesis and then continue during key stages of the IP and SoC design process.
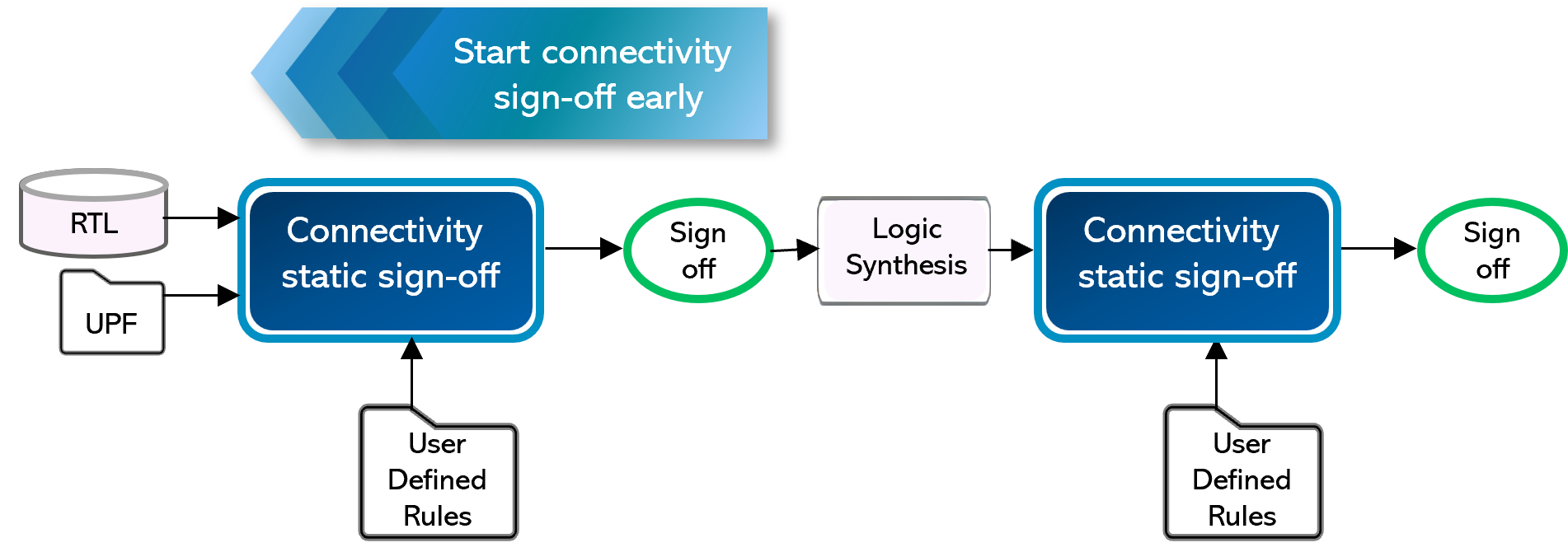
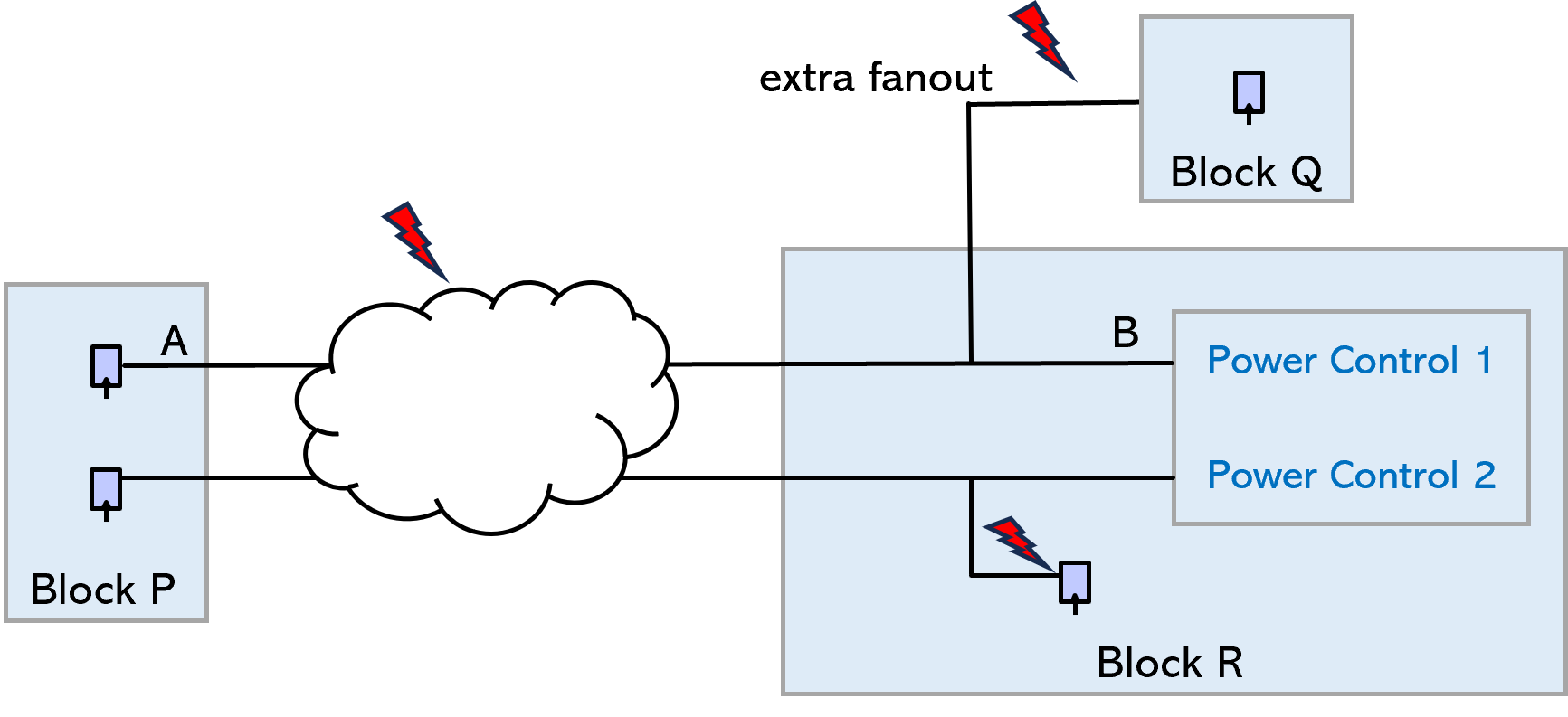
RTL design stage: Validate connectivity for memory, power, and debug logic, and avoid glitches. Identify & remedy improper connections that could create complications when blocks are placed side by side in physical design.
Post-synthesis stage: Re-run connectivity checks on the synthesized netlist to uncover new issues introduced — especially around power rail crossings, DFT, and debug logic that could affect implementation or test.
Abutment connectivity checking
An example of how significant benefit can be achieved with early verification is abutment connectivity checking.
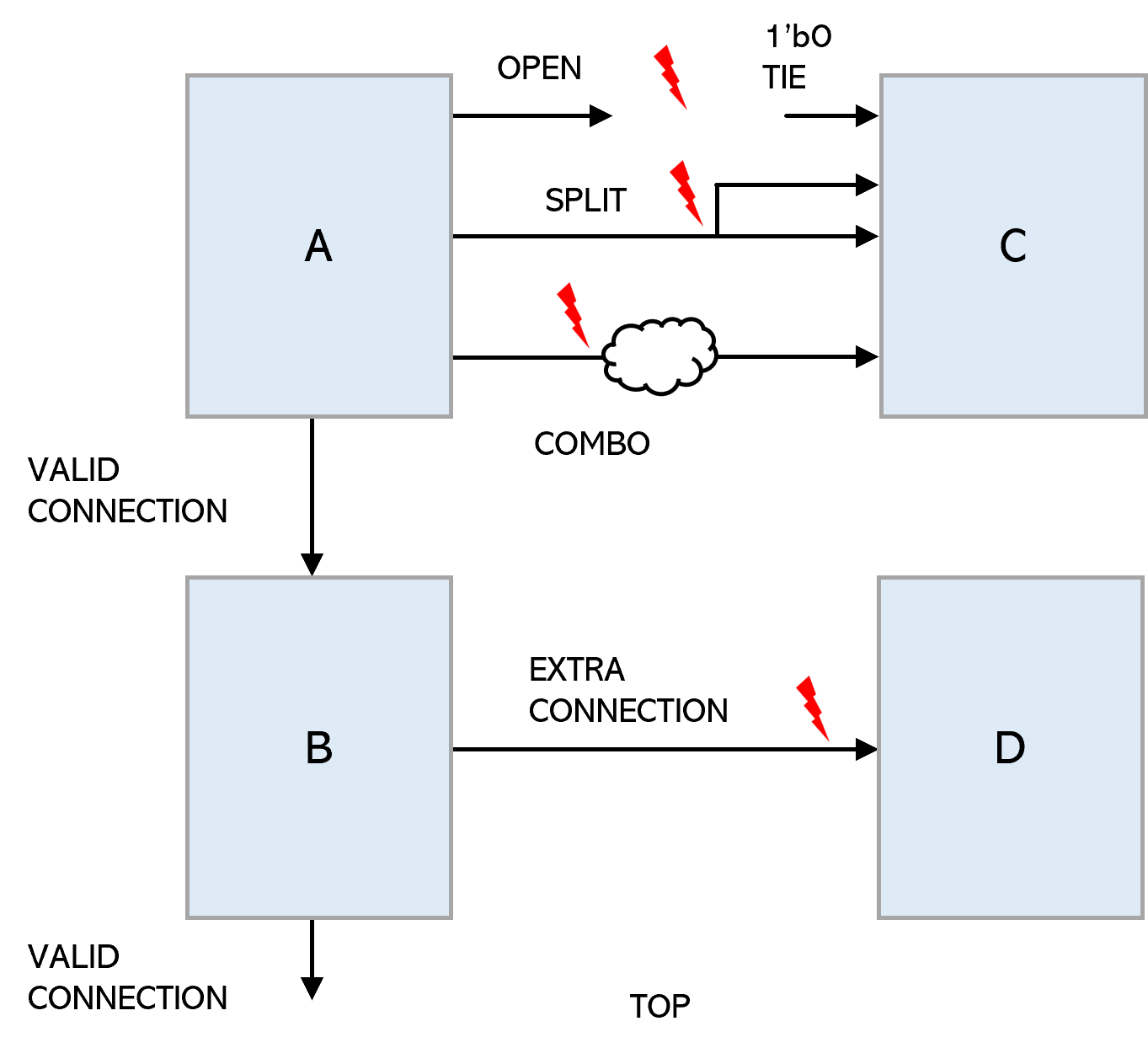
Some blocks are abutted in the physical layout and need to follow strict rules to avoid design failures. Ensuring compliance of the expected connectivity at RTL level can proactively avoid finding issues later.
For the blocks to be abutted, various checks, e.g., open, tie, split, combo, loopback, and extra connection should be performed. As shown here, the allowed arcs show top-level instances that are to be checked for abutment compliance.
Allowed Arcs = { A B } { A C } { * TOP }
3. Understand connectivity static sign-off’s critical differences from formal, simulation & TCL scripting
Below is a comparison of connectivity static sign off with formal, simulation, TCL scripting approaches.
3a. Formal verification vs. Static sign-off
Exhaustive verification. Both connectivity static sign-off and formal methods perform exhaustive verification, but the combination of static sign-off’s speed and capacity enables it to fully analyze both short, simple paths and complex paths with multiple sources and destinations.
Performance. Static sign-off has analyzed tens of millions of gates in about 30 minutes — including reading the design to create the database — with only a few minutes of analysis time.
This is orders of magnitude faster than formal verification, which can take hours. Static sign-off also performs well on a single CPU, while formal requires multiple cores. Memory usage for static sign-off is estimated to be less than 1 GB per million gates.
Capacity. Static sign-off can analyze billions of gates in a few hours — without requiring black boxing. This can include checking millions of paths from multiple sources to destinations very efficiently.
Formal verification, however, typically supports only a few million gates, even after using multiple processing cores for analysis.

Connectivity static sign-off’s performance is orders of magnitude faster than formal methods
3b. Simulation vs. Static sign-off
Coverage. With simulation, coverage depends on test vectors, testbenches, and VIP availability. The checks only cover conditions explicitly specified in the test vectors, so designers cannot guarantee all conditions are covered. Additionally, to try to do glitch checking during simulation, an engineer would write assertions to do limited glitch checking for specific points.
Static sign-off user-defined rules automatically cover all conditions. If the engineer specifies a source/destination pattern, it will cover all combinations.
Similar to simulation, connectivity static sign-off checks that the destination has the expected value for specified source and constraint values providing the basic expected checks.

Checking expected value at a destination
Feasibility. Certain checks are only feasible in static sign-off — and not simulation. Some examples are:
1. Confirming bus bits aren’t swapped (see 1a, ex 2)
2. Verifying only one source drives multiple destinations (see 1a, ex 3)
3. Checking physical connectivity early by verifying proper abutment (see 1b)
4. Confirming that a connection does not exist
- Static sign-off will flag that the specific connection does not exist– in any situation.
- Simulation will not flag that connection does not exist — if other signals drive destination to the expected value.
Does connection from A to B exist?
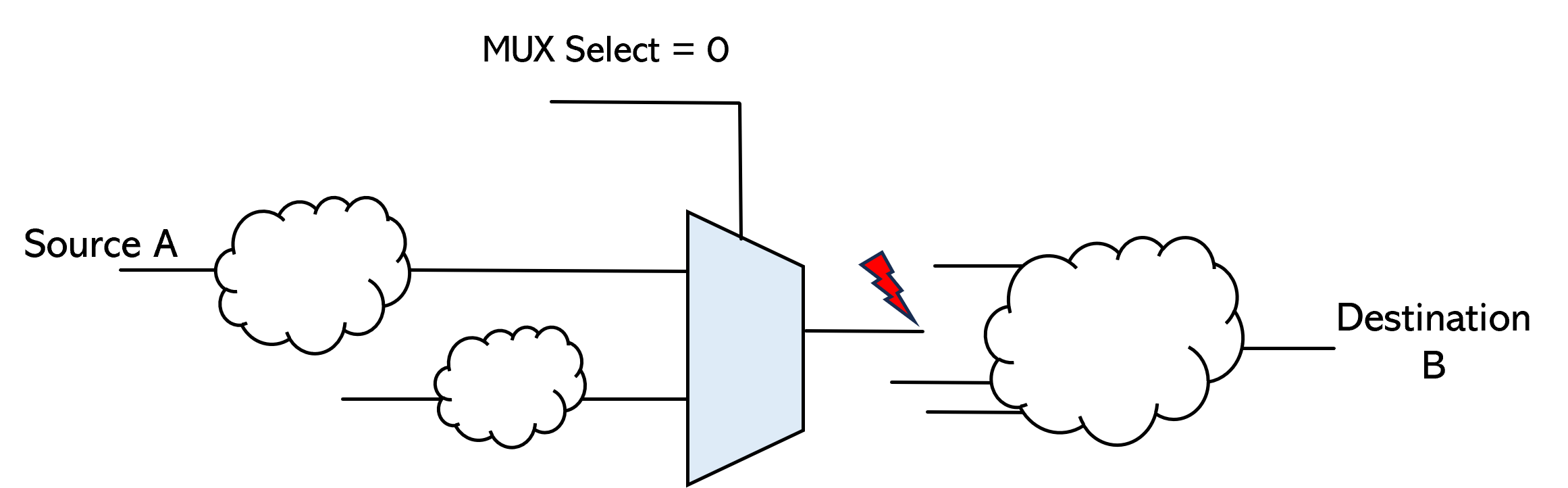
5. Confirm there is no extra fanout
- Static sign-off will check whether A is connected to B, and check for an extra fanout
- Simulation will only check that A is connected to B. It cannot check for an extra fanout

Is there an extra fanout?
Further, because static sign-off rule creation is not dependent on test vectors or test bench availability, the sign-off step can start very early in RTL design.
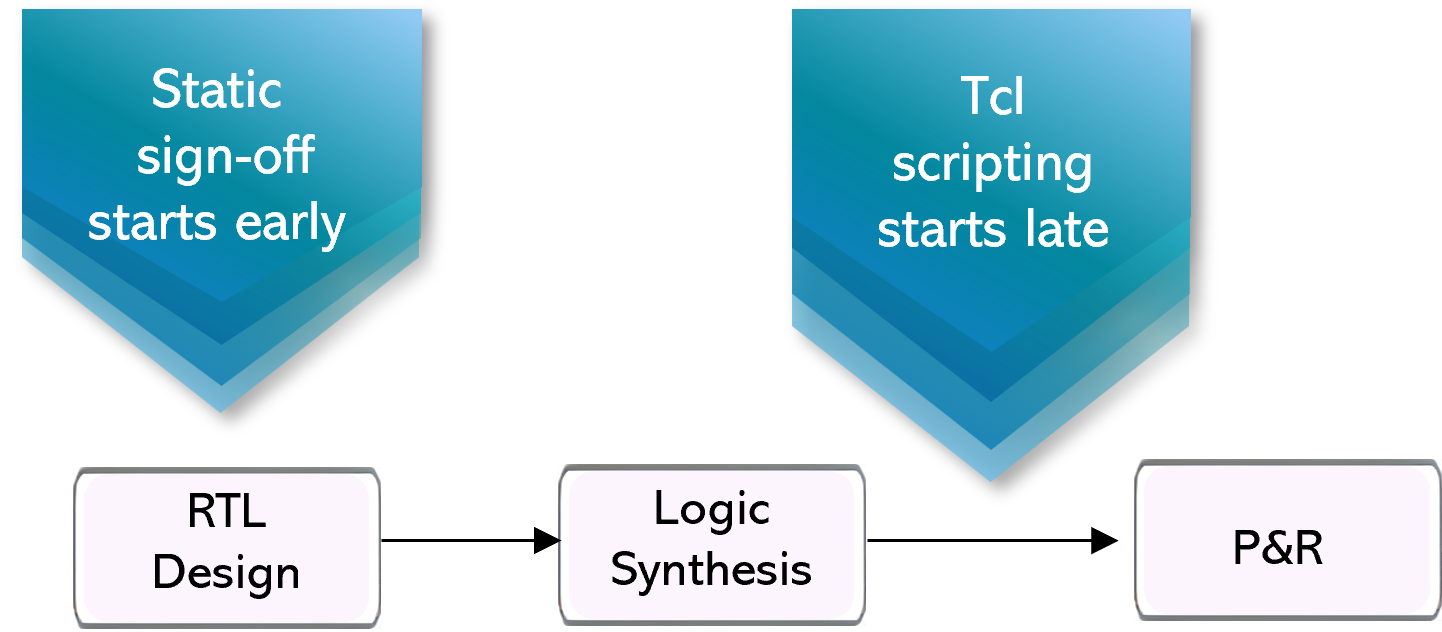
3c. Tcl scripting vs. Static sign-off
Rule Creation. Tcl scripts require complex coding and ongoing maintenance for connectivity checking. In contrast, static sign-off uses efficient, flexible commands with minimal rule specification or maintenance effort.
Performance. Tcl scripts take hours to run just one block, which static sign-off can complete in minutes.
Early vs. late sign-off. Tcl scripts run only on netlists, so checks do not occur until after synthesis. Static sign-off can be run during RTL, enabling early detection of connectivity errors and reducing unnecessary iterations.
3d. RTL linting vs. Static sign-off
RTL linting sign-off is focused on ensuring RTL quality for the selected rules. Connectivity static sign-off goes further, understanding more of the design’s functionality, including power, and performing more explicit checks across the entire design. It also supports constraint-based connectivity and glitch checking.
4. Tool usability can make or break a sign-off methodology
For a connectivity verification and sign-off tool to be widely adopted in the design methodology, it’s essential that the tool be easily incorporated and minimize designer effort.
Below are six key factors to consider when evaluating a connectivity verification and sign-off tool.

Fast Performance
When a tool can analyze 100 million gates in only minutes, it becomes feasible for engineers to run connectivity sign-off as part of the design process.
Connectivity error-free designs become feasible if the tool has the capacity to sign off multi-billion gate SoCs.
![]()
Low-Noise Reporting
Low-noise reporting reduces review & debug time. This can be achieved if irrelevant issues can be filtered out by specifying conditions or constraints on structural checks. Automatic violation classification into sub-check categories (source/destination miss, bit flips…) gives designers precise control over which rules & sub-checks are analyzed and reported.
![]()
User-defined, flexible rules
The connectivity checks needed depend on the design requirements. Thus, engineers must be able to quickly define compact rules for various source-destination combinations, connection types, & glitch checks. The tool should allow flexible rule definitions, both broad & specific, e.g., capturing all flops or limiting to a particular module, and support place-and-route rules such as abutment checking.
![]()
Efficient Rules Creation
Efficient ruleset creation can save weeks, avoid manual errors, and improve coverage.
For example, the tool should require only a few commands to define a block-level or SoC-level check to verify the validity of a connection.

Automated object aggregation
A connectivity-checking tool should automatically aggregate key objects for checks, such as power control objects like isolation cells, which are spread across the chip.
Manually collecting them is impractical, so the tool should allow designers to automatically create groups of objects, either chip-wide or within a specific hierarchy.

Negative Tests, Mutually Exclusive, Custom Groups
The tool should check for both connectivity and non-connectivity and allow engineers to automatically create custom object groups (e.g., for signals or instances). One command should generate the desired objects dynamically, while another can utilize those groups. Additionally, it should report mutually exclusive connections, such as violations like “If A → B, then C → B is not allowed” or “If X → Y, then X → Z is not allowed,” and automatically identify and flag these connection violations.
5. Glitch checking is needed to ensure connection integrity
Connectivity checking should include glitch checking to be complete. A glitch is a signal transition with a duration shorter than the system clock period. Glitches can lead to functional failures— especially when they occur on untimed paths.
A transition on the select line of a multiplexer can induce a glitch at the MUX output due to unequal combinational delays along the data input paths. This glitch can propagate through downstream combinational logic and arrive at the input of a receiving flip-flop.
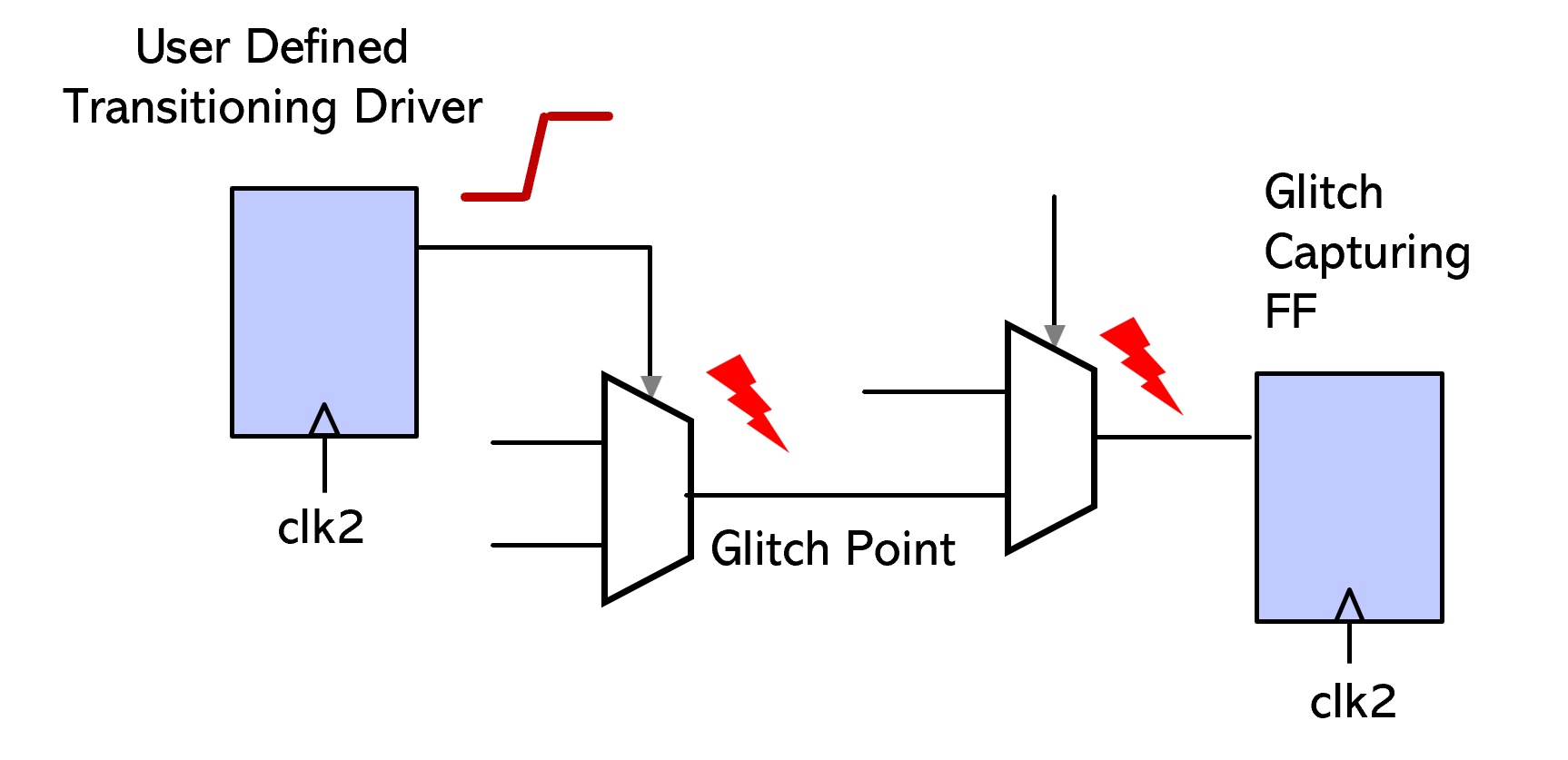
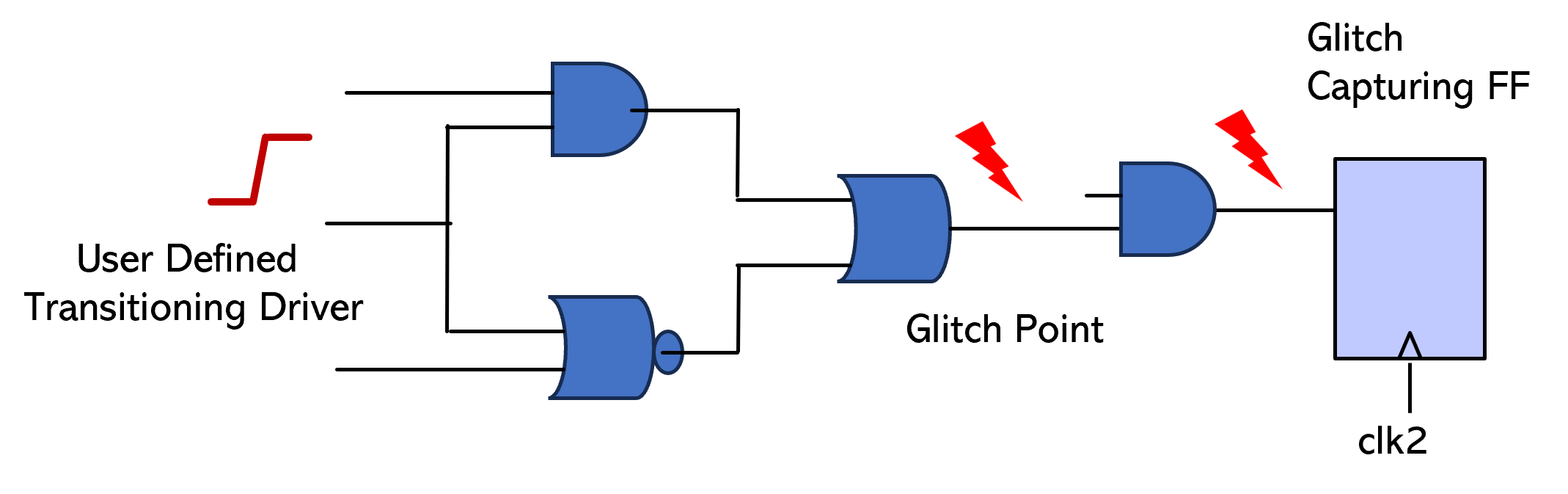
If the transition occurs near a clock edge, it may violate timing constraints or place the flip-flop in an indeterminate state, potentially resulting in functional errors. On untimed paths, a glitch can cause unexpected system behavior leading to functional failures.
III. Conclusion: Maximizing connectivity sign-off efficiency
The role of static sign-off continues to expand, with connectivity static sign-off offering design teams user-defined rules, fast performance, low noise, and broadest coverage — eliminating the limiting restrictions associated with formal verification, simulation and Tcl scripting.
About Real Intent SafeConnect
Real Intent SafeConnect connectivity & glitch sign-off tool meets all the key connectivity verification metrics discussed above, eliminating missed errors while minimizing designer effort.
1. Analyzes 10s of millions of gates in only minutes
2. Creates low noise violation reports, with filtering & control over checks & sub-checks
3. Supports user-defined rules
4. Offers efficient ruleset creation — saving weeks
5. Allows negative testing, mutually exclusive rules, & automatic custom object groups
6. Performs glitch checking to ensure physical connectivity integrity

ABOUT THE AUTHOR
Prakash Narain, President & CEO of Real Intent
Dr. Prakash Narain shifted Real Intent’s technology focus to Static Sign-Off to better tackle verification inefficiencies back in 2010. Since then, Prakash has expanded this effort to now offer a broad set of tools focused specifically on different static sign-off domains, including CDC, RDC, DFT and others — with more coming.
His career spans IBM, AMD, and Sun where he had hands-on experience with all aspects of IC design, CAD tools, design and methodologies. He was the project leader for test and verification for Sun’s UltraSPARC III, and an architect of AMD’s Mercury Design System. He has architected and developed CAD tools for test and verification for IBM EDA.
Dr. Narain has a Ph.D. from the University of Illinois at Champaign-Urbana where his thesis focus was on algorithms for high level testing and verification.
